This is the multi-page printable view of this section.
Click here to print.
Return to the regular view of this page.
Policies
Policies are rules that allow you to customize the behavior of the Endor Labs scan.
You can use policies to:
- Enable, disable, or edit out-of-the-box features
- Create custom findings
- Set guardrails for the development process
- Create custom ticketing or messaging workflows
Endor Labs comes with various out-of-the-box policies that enable you to quickly get started with the product. Policy templates are available to help you easily create custom findings and configure workflows around known vulnerabilities, outdated, unmaintained, or unused software dependencies, license risks, code review guidelines, repository configurations, and more.
Note: See also configure policy settings.
You can also write policies from scratch using Rego policy language and customize policies based on organizational rules and needs.
Policy types
You can set up the following types of policies in Endor Labs.
-
Finding policies - Enable or disable out-of-the-box features and create custom finding policies to identify and raise findings for issues in your development environment. For example, you can create a finding policy to raise findings for missing, unknown, problematic, or incompatible licenses.
-
Exception policies - Identify findings that should be exempt from action policies. For example, you can create an exception policy to automatically dismiss all findings found in the serverless-dns package.
-
Action policies - Define the system behavior and set up workflows when a finding with a given set of properties is raised. For example, you can create an action policy to create a Jira task when packages with outdated dependencies are included in your projects.
-
Remediation policies - Define the conditions to remediate findings when an upgrade is available. For example, you can apply remediation when a low risk upgrade is available.
Key benefits
Policies are essential to define risk tolerance, set automated rules for open source components, check your repository or organization configuration, and more.
- Identify and triage issues - Policies give you a quick and automated way to identify and triage issues in your environment. This saves valuable development time and ensures developers consider security issues at the early stages of application development.
- Improve decision-making - Automating enforcement simplifies decision-making in an organization and reduces complexity. Policies make assessing the OSS components simpler and allow developers to focus on violations critical to the organization.
- Establish governance - Use policies to set up an organization’s governance methods such as enforcing Multi-Factor Authentication, setting up code review guidelines, guidelines on the use of the open source components, preventing misconfiguration of source code repositories, and more.
1 - Finding policies
Learn about finding policies and how to use them.
All findings are enabled, disabled and/or customized via policies. There are three types of Finding Policies:
- Open-source software management - Enable or disable findings for Vulnerabilities and Malicious Packages, Outdated Dependencies, Unmaintained Dependencies, Unpinned Direct Dependencies, Unused Direct Dependencies, License Risks
- Repository security posture management configuration - Enable, disable, or customize out-of-the-box policies repository security posture management (RSPM)
- Custom - Create custom policies from scratch or from pre-defined policy templates
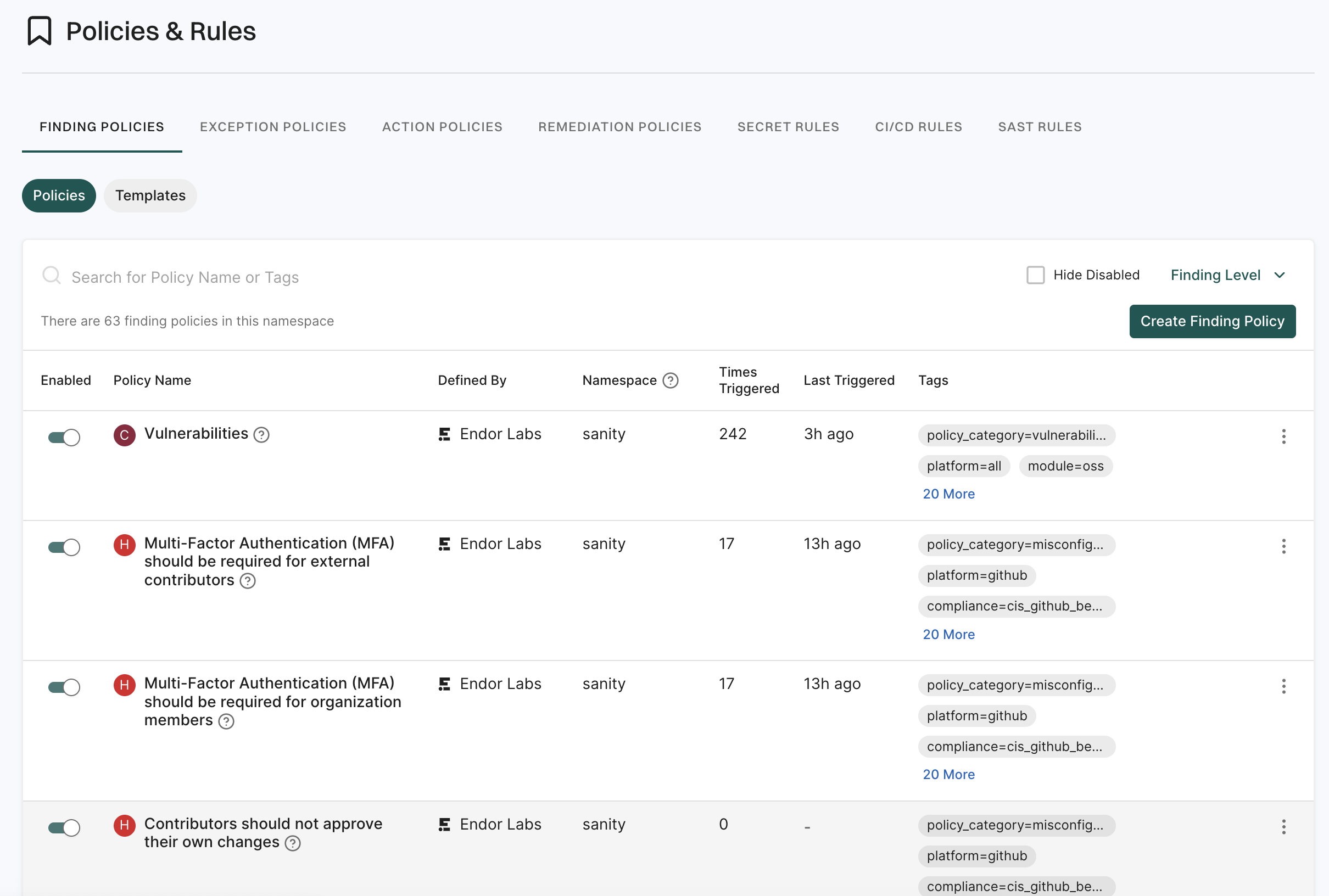
Manage finding policies
You can view, enable, disable, edit, upgrade, or delete your Endor Labs finding policies.
- Sign in to Endor Labs and select Policies & Rules from the left sidebar.
- Click Finding Policies to view the list of finding policies.
- You can use the search bar to search for a policy.
- Use the toggle next to a finding policy to enable or disable the finding policy.
- Select Hide Disabled to hide policies that are not enabled.
- Use Finding Level to filter policies by Critical, High, Medium, or Low.
- To edit a policy, click the vertical three dots and select Edit.
- To delete a policy, click the vertical three dots and select Delete. The findings associated with the policy are not deleted.
Upgrade a finding policy
Upgrades are available when there are changes to a policy, such as new fields, parameters, tags, or updates to the Rego code.
After upgrading a policy, you can’t revert it to its previous version.
-
To upgrade a policy based on the latest template version, click the vertical three dots and select Upgrade.
-
In Upgrade Available for Policy, review the release notes and select Upgrade Policy.
You can enable automatic policy upgrades from the Policies & Rules system settings. See configure policy settings for more information.
Custom finding policies
Create custom finding policies to identify additional issues based on the needs of your organization. For example, you can create license violation policies to define the behavior for missing, unknown, problematic, or incompatible licenses. You can permit or restrict packages with certain license types.
Endor Labs provides finding policy templates for various use cases:
Create a finding policy from template
Create a finding policy from a pre-defined Endor Labs template.
- Sign in to Endor Labs, and select Policies & Rules from the left sidebar.
- Click Create Finding Policy.
- Choose From Template to create a finding policy from template.
- Choose a Policy Template from the list. The template details are pre-filled with recommended values on the form.
- Severity, Summary, Explanation, Remediation, Finding Name, and Finding Categories are pre-populated with Endor Labs’ recommended values. You can modify them to suit your requirements.
- In Finding Custom Tags, enter custom tags that you want to associate with the findings of this policy. Custom tags can have a maximum of 63 characters and can contain letters, numbers, and characters = @ _ -. Note that these are different and separate from the system defined finding tags.
- You can Assign Scope to the finding policy by specifying what projects the policy has to scan.
- In Inclusions, enter the tags of the projects that you want to scan.
- In Exclusions, enter the tags of the projects that you do not want to scan. Exclusions take precedence over the inclusions, in case of a conflict.
- Click the link to view the projects included in the finding policy scan.
- You can set custom tags for your projects from Projects > Settings > Custom Tags. See also Tagging projects.
- If your policy has both include and exclude tags, and a project matches both, the exclude tag takes precedence, and the policy won’t apply to that project.
- Name Your Finding Policy.
- Enter a human readable Name for your finding policy.
- Enter a Description for your finding policy that describes what it does.
- Enter any Policy Tags that you want to associate with your policy. Tags can have a maximum of 63 characters and can contain letters, numbers, and characters = @ _ -.
- Advanced: When you define a policy you do so for the current namespace and all child namespaces. If you do not want the policy to be applied to any child namespaces, click Advanced and deselect Propagate this policy to all child namespaces.
- Click Create Finding Policy. The policy will be enabled by default.
Create a finding policy from scratch
Write a finding policy from scratch using the OPA Rego policy language.
-
Sign in to Endor Labs, and select Policies from the left sidebar.
-
Click Create Finding Policy.
-
Choose From Scratch to author a finding policy from scratch.
-
Enter the Rego rule for the policy in Rego Definition. For instance, the following Rego rule identifies dependencies with an Endor Labs overall score lower than 7.
package examples
match_package_version_score[result] {
some i
data.resources.Metric[i].meta.name == "package_version_scorecard"
data.resources.Metric[i].meta.parent_kind == "PackageVersion"
data.resources.Metric[i].meta.parent_uuid == data.resources.PackageVersion[_].uuid
score := data.resources.Metric[i].spec.metric_values.scorecard.score_card.overall_score
score < 7
result = {
"Endor": {
"PackageVersion": data.resources.Metric[i].meta.parent_uuid
},
"Score": sprintf("%v", [score])
}
}
-
Enter the OPA Query Statement for the rule in the following format: data.<package-name>.<function-name>. For the example, the query statement is data.examples.match_package_version_score in the above Rego rule.
-
Select the Resource Kinds required to evaluate the policy. For the example above the required resource kinds are PackageVersion and Metric.
-
In Group by Fields, if applicable, list which custom output fields to group the findings by in addition to the resource UUID. Use this optional field if you want to be able to raise multiple findings against the same finding target. For example, a repository version may have multiple exposed secrets and thus there are multiple findings of the same type for the same repository version.
Note that you do not need to add all (or any) custom fields here, just the ones you want to be used to group the matches by.
-
Choose a Severity for the generated finding.
-
Enter a short Summary of the finding.
-
Enter an Explanation for the finding. You can include additional information or explain why this finding is important.
-
Describe how to mitigate the finding in Remediation.
-
Enter the Finding Name.
-
Select one or more categories for the finding in Finding Categories.
-
See steps 6-10 above under Create a finding policy from template
Note: The application verifies the Rego syntax and query statement before creating the policy. However, please note that the logic cannot be fully validated without input data. See also validate policy.
Available resource kinds
Every policy must specify the resource kinds it needs to execute the Rego logic. Requested resource kind objects for the current scan are made available to the Rego code under data.resources.<ResourceKind>. The following resource kinds are available:
Finding targets
Findings are raised against finding targets.
Findings targets have one of three resource kinds:
- Repository (for example, default branch protections)
- RepositoryVersion (for example, CI/CD coverage, secrets)
- PackageVersion (for example, vulnerabilities, scores, licenses)
Individual finding target records are identified by their universally unique identifier (UUID).
The finding target record is the parent of the finding record.
Note: The finding target resource kind is PackageVersion for findings in the root package as well as for findings in its dependencies. A dependency PackageVersion record may or not be in the same namespace as the root package. The relationships between the root package and its dependencies is captured by the corresponding DependencyMetadata records. All DependencyMetadata records are children of the root PackageVersion record in the same namespace as the root PackageVersion.
All finding policies must generate the finding payload as json data, listing the finding target resource kind and UUID under “Endor” in the following format.
foo[result] {
<match conditions>
result = {
"Endor": {
<resource-kind>: <resource-uuid>
},
<custom-key>: <custom-value>
}
}
Custom output fields
Custom key-value pairs are optional. The value is treated as a single string and must be formatted accordingly.
If a custom key is specified in the Group by Fields list then the value is appended to the finding name (the key is not included). Example: SSL disabled for Webhook ID #444611302, where SSL disabled for Webhook is the value of the Finding Name field and ID #444611302 is the value of a custom key.
Otherwise, both the key and the value are listed at the end of the finding summary on a new line for each pair. Example: Score: 4.10.
Validate policy
See the endorctl validate policy command for details on how to validate a custom policy and inspect the matches returned for a given project.
1.1 - CI/CD tool policies
Learn about the predefined finding policy templates for CI/CD tools used in your software development environment.
Endor Labs provides the following finding policy templates for detecting CI/CD tool usage.
See Finding Policies for details on how to create policies from policy templates.
| Policy Template |
Description |
Severity |
| Unauthorized tool usage |
Raise a finding if a repository uses a tool that is specifically not approved by the company policy. |
Medium |
| Require tool category |
Raise a finding if a repository does not have any tools in a required tool category. |
Medium |
| Require tool |
Raise a finding if a required tool is not detected in a repository. |
Medium |
1.2 - Container policies
Learn about the predefined finding policy templates for containers.
Endor Labs provides the following container image finding policy template to detect a if a base image is not permitted by an organization.
See Finding Policies for details on how to create policies from policy templates.
| Policy Template |
Description |
Severity |
| Permit only trusted base images for container images |
Raise a finding if a container image uses a base image not approved by the company policy. |
Critical |
1.3 - License policies
Learn about the predefined finding policy templates for open source license risk management.
Policy templates for open source license detection
Endor Labs provides the following policy templates for detecting open source license usage.
See Finding Policies for details on how to create policies from policy templates.
| Policy Template |
Description |
Severity |
| Permit only specified software licenses |
Use this template to define an allowed list of software licenses permitted within your organization or a subset of projects. Endor Labs will raise findings when dependencies in packages or projects have licenses that are not on the allowed list. |
Medium |
| Restricted software licenses |
Use this template to define a blocked list of software licenses that should be restricted from use or only used within specific contexts within your organization. Endor Labs will raise findings when dependencies in packages or projects have licenses that are on the blocked list. |
Medium |
| Restricted software license types |
Use this template to create an organizational policy to restrict certain license types or limit a license type to specific contexts within an organization. This is useful to identify license risks and violations in 3rd party open source packages. The license type classification in this policy follows the industry best practice rules defined by Google license types. If no license types are specified using the input parameter, only “restricted” and “FORBIDDEN” license types are flagged. |
Medium |
1.4 - Open-source policies
Learn about the out-of-the-box finding policies for open source risk management.
Open source risk policies generally fall into one of several categories:
- Vulnerabilities - Known vulnerabilities associated with a software component.
- Operational Risk - Issues that may make it more expensive to address any application impacting bug, including a security vulnerability.
- License Risk - Issues that may cause legal or compliance risk associated with your software.
Policies for open source risk management
Endor Labs comes with the following out-of-the-box finding policies to detect open source risks.
See Finding Policies for details on how to enable or disable out-of-the-box policies.
| Policy |
Description |
Severity |
| Vulnerabilities |
Vulnerabilities indicate security weaknesses or flaws in the dependencies used by a software project. They can pose risks to the overall security and stability of a project. Raises findings for projects where vulnerabilities are detected. |
Critical |
| Flag Phantom Dependencies |
Raises findings for dependencies that are used in source code but not declared in the package’s manifest files. These dependencies are called phantom dependencies and are detected during deep scans. They are not detected during a --quick-scan. |
Medium |
| License Risks |
Raises findings for dependencies where the repository is either missing a license or has license related problems, for example multiple conflicting licenses. |
Medium |
| Outdated Dependencies |
Outdated dependencies are software libraries, frameworks, or modules that are being used in a project but have newer versions available. They are usually superseded by newer releases that offer bug fixes, security patches, improved functionality, or better performance. Raises findings for projects with outdated software libraries, frameworks, or modules. |
Medium |
| Unmaintained Dependencies |
Unmaintained dependencies refer to external libraries, frameworks, or modules that are no longer actively maintained or supported by their developers. These dependencies may have reached end-of-life, without updates, bug fixes, security patches, or any form of support. Raises findings for projects with unmaintained packages. |
Medium |
| Unpinned Direct Dependencies |
Unpinned direct dependencies indicate the absence of a specific version or range of versions for a dependency. This can lead to potential issues because different versions of dependencies may introduce changes, bug fixes, or even breaking changes, which can impact the project’s behavior or stability. Raises findings for projects with unpinned dependencies. |
Medium |
| Unused Direct Dependencies |
Unused direct dependencies are listed in a project’s configuration or dependency file and are not utilized or referenced in the project’s source code. Raise findings for projects with unused direct dependencies. |
Medium |
| Low Endor Activity Scores |
Projects with low Endor Labs activity scores are less likely to be kept up to date. They are susceptible to software bugs and security risks. Raise findings for packages with low Endor Labs activity scores. |
Low |
| Missing Source Code |
If you cannot audit the source code associated with a software component, there is limited visibility that can result in operational and security risks. Raises findings for packages with missing source code. |
Low |
| Low Endor Quality Scores |
Projects with low Endor Labs quality scores are highly likely to be susceptible to security and operational risks. Raise findings for packages with low Endor Labs quality scores. |
Low |
| Potential Typosquats |
Typosquat is a malicious practice where a domain name closely resembles popular or legitimate domain names but contains typographical errors. This can deceive or exploit users who make mistakes while typing the intended website’s URL or package name. Raises findings for packages that contain potential typosquats. |
Low |
| Low Endor Popularity Scores |
A popularity score indicates how well the software component is being used by developers. Raise findings for repositories that have low popularity scores. |
Low |
1.5 - RSPM policies
Learn about the out-of-the-box finding policies for repository security posture management (RSPM).
Strong information security practices are necessary to secure your open source code used in your development and delivery infrastructure.
Policies for repository security posture management
Endor Labs comes with the following out-of-the-box policies that help you determine the effectiveness of your security practices.
See Finding Policies for details on how to enable, disable, or edit out-of-the-box policies.
| Policy |
Description |
Severity |
| Archive inactive repositories |
Repositories that are not actively maintained are vulnerable to security breaches. Archiving such repositories helps maintain a cleaner and more organized GitHub environment. Archiving ensures repositories become read-only, thus preventing unauthorized modifications. Raise findings for repositories that have been inactive beyond the duration specified by the user, defaulting to 6 months if not specified. |
High |
| At least two administrators should be configured for a repository |
Having fewer than two administrators for a repository may cause problems when the administrator is unavailable. A minimum of two administrators must be configured to meet this requirement. |
Medium |
| Authorization to push or merge to protected branches should be limited |
Limiting the authorization to push or merge code to protected branches is a best practice in software development workflows. By restricting access to protected branches, you maintain control over code changes and ensure that only authorized individuals can make modifications. Raises findings for repositories that do not enforce rules around merging code to protected branches. |
Medium |
| Branch protection rules should be enforced on administrators |
Enforcing branch protection rules on administrators is a best practice in software development workflows. By applying branch protection rules to administrators, you ensure that even privileged individuals follow the established processes and adhere to the same standards as other team members. Raises findings for repositories that do not enforce branch protection rules. |
Medium |
| Branches should be up-to-date before merging |
Ensuring that branches are up-to-date before merging is a best practice in software development. It avoids conflicts, helps in the early detection of issues, and maintains code coherence. Raise findings for repositories that do not enforce rules on branches to be up-to-date before merging. |
Medium |
| Code owner review is required when a change affects owned code |
Code owner review is a practice in software development where specific individuals or teams are designated as code owners for certain parts of the codebase. When a change is proposed that affects code owned by a particular individual or team, a code owner review is required before the change can be merged into the main codebase. |
Low |
| Code owner should be configured for sensitive code |
Code owner review is a best practice in software development workflows where specific individuals or teams are designated as code owners for certain parts of the codebase. When a change is proposed that affects code owned by a particular individual or team, a code owner review is required before the change can be merged into the main codebase. Raises findings for repositories that do not enforce code owner reviews. |
Low |
| Comments should be resolved before merging |
Resolving comments ensures that all feedback, questions, and issues raised during the code review process have been addressed satisfactorily before the code is considered ready for integration. Raises findings for repositories that do not resolve comments before merging. |
Low |
| Commits should be signed for new changes |
Requiring commits to be signed for new changes is a best practice in software development workflows. Commit signing involves using digital signatures to verify the authenticity and integrity of the commit. Raises findings for repositories that do not enforce signed commits. |
Medium |
| Contributors should not approve their own changes |
Robust code reviews are essential and contributors should not approve their own changes in a collaborative software development environment. Raises findings for repositories that do not enforce code reviews. |
High |
| Default member permissions should be restricted |
As a best practice, set the base permissions for members in an organization to either “read” or “none” on GitHub. Restricting member permissions controls the access over repositories and prevents misuse. |
Medium |
| Dismissing Code Change Reviews should be restricted |
Restricting the ability to dismiss code change reviews is a best practice in software development workflows. Dismissing code change reviews should be limited to specific cases and authorized individuals to ensure accountability, maintain code quality, and promote a collaborative and transparent review process. Raises findings for repositories that do not enforce rules around dismissing code reviews. |
Medium |
| Ensure branch protection is enforced for the default branch |
Branch protection rules allow you to set controls over your software development processes. The default branch for this repository has no branch protection rules and should be protected. |
High |
| Force pushing code to protected branches should be restricted |
Restricting the ability to force push code to protected branches is a best practice in software development workflows. Restricting this action helps maintain code integrity, accountability, and collaboration. Raises findings for repositories that do not enforce rules around pushing code to protected branches. |
Medium |
| Linear commit history should be required |
Linear comment history indicates a chronological sequence of commits made to a code repository. It provides a clear and chronological view of the code changes made to a repository, aiding in code navigation, collaboration, and bug tracking. Raises findings for repositories that do not have linear commit history. |
Low |
| Missing Source Code |
If you cannot audit the source code associated with a software component, there is limited visibility that can result in operational and security risks. Raises findings for packages with missing source code. |
Low |
| Multi-Factor Authentication (MFA) should be required for external contributors |
Multi-Factor Authentication adds an additional layer of security to access accounts or systems and prevents unauthorized access to code repositories. Raises findings for repositories that do not enforce MFA for external contributors. |
High |
| Multi-Factor Authentication (MFA) should be required for organization members |
Multi-Factor Authentication adds an additional layer of security to access accounts or systems and prevents unauthorized access to code repositories. Raises findings for repositories that do not enforce MFA for members in their organization. |
High |
| Organization webhooks must be configured with a secret |
The authenticity of a webhook payload cannot be verified when it is set up without a secret key. Anyone could send forged payloads to the organization’s webhook endpoints leading to security issues. |
Medium |
| Organization webhooks should use HTTPS |
A webhook URL is used to send notifications, along with a payload, to designated internet endpoints. Given that the payload contains sensitive information, all webhooks must be directed toward endpoints secured by HTTPS. |
Medium |
| Organization webhooks should use SSL verification |
When Organization webhook SSL verification is disabled, GitHub is explicitly instructed not to verify the identity of the remote server it is sending information to. This configuration bypasses standard security controls in the HTTP protocol, which are designed to prevent attackers from executing man in the middle attacks. |
Low |
| Organizations should be verified |
The Organization Verified badge on GitHub is a visual indicator that signifies an organization’s authenticity and official status. It helps users identify legitimate and trusted organizations on the GitHub platform. Raise findings for organizations that are not verified. |
Low |
| Organizations should have fewer than three owners |
Organization administrators have the highest level of permissions, including the ability to add/remove collaborators, create or delete repositories, change branch protection policy, and convert to a publicly accessible repository. Due to the permissive access granted to an organization administrator, it is highly recommended to have at most three administrator accounts. |
Medium |
| Private repositories should not permit forking |
Allowing forking in repositories within an organization can compromise data security, potentially exposing sensitive information to unauthorized parties. It exposes vulnerabilities in the codebase, making it more susceptible to exploitation. Additionally, tracking changes across multiple forks becomes complicated. |
Low |
| Protected Branch Deletion should be blocked |
Protecting branch deletion, especially for critical branches, is a best practice in software development workflows. Raises findings for repositories that do not enforce rules around protected branch deletion. |
Medium |
| Repository webhooks must be configured with a secret |
The authenticity of a webhook payload cannot be verified when it is set up without a secret key. Anyone could send forged payloads to the repository’s webhook endpoints leading to security issues. |
Medium |
| Repository webhooks should use HTTPS |
A webhook URL is used to send notifications, along with a payload, to designated internet endpoints. Given that the payload contains sensitive information, all webhooks must be directed toward endpoints secured by HTTPS. |
Medium |
| Repository webhooks should use SSL verification |
When repository webhook SSL verification is disabled, GitHub is explicitly instructed not to verify the identity of the remote server it is sending information to. This configuration bypasses standard security controls in the HTTP protocol, which are designed to prevent attackers from executing man in the middle attacks. |
Low |
| Require a SECURITY.md file |
A SECURITY.md outlines security practices, reporting procedures, and guidelines for handling security-related issues within a project. It is included in the root directory of software repositories. Raise findings for repositories that do not include a SECURITY.md file. |
Low |
| Restrict general action permissions to organization members |
Setting general action permissions for the organization to “all” can pose security risks by allowing unrestricted access to repositories to use GitHub actions. This ensures that actions within the organization are confined to local resources, mitigating the risk of unauthorized access or unintended actions on external resources. |
High |
| Restrict the creation of repositories to trusted members |
Limiting repository creation to trusted users and teams is advisable for maintaining organizational structure, reducing tracking workload, preventing impersonation, and avoiding overloading the version-control system. |
Medium |
| Stale approvals should be dismissed |
To prevent malicious code from being introduced into a codebase, it is important to have a robust approval process for code changes. When changes are made to a proposal, outdated approvals must be declined, and previously accepted code changes must be re-evaluated. The approval process should involve multiple reviewers, and organizations should also consider implementing automated code analysis and security testing. |
Medium |
| Status checks should pass before merging new code |
Ensuring that status checks pass before merging new code is a best practice in software development workflows. Status checks serve as automated checks or validations that assess the quality, integrity, and readiness of the code changes before they are merged into the main codebase. Raises findings for repositories that do not enforce status checks before merging new code. |
Medium |
| Two informed reviews should be required for code changes |
Requiring two informed reviews for code changes is a best practice in software development. It helps ensure that code changes are thoroughly examined, promotes collaboration, and increases the overall quality of the codebase. Raises findings for repositories that do not enforce two reviews for code changes. |
Medium |
| Workflows should not be allowed to create and approve pull requests |
Allowing workflows to create and approve pull requests within an organization can enable users to evade code-review protocols. Attackers could exploit this by establishing workflows that autonomously approve their pull requests and merge them discreetly. Consequently, they can introduce potentially harmful code into the production system. |
High |
1.6 - Secret policies
Learn about the out-of-the-box finding policies and templates for secret detection.
Policies for secret detection
Endor Labs comes with the following out-of-the-box finding policies to detect leaked secrets.
See Finding Policies for details on how to enable, disable, or edit out-of-the-box policies.
Note: The out-of-the-box secret policies can be deleted and re-created from the corresponding policy templates. See Policy templates for secret detection below.
| Policy |
Description |
Severity |
| Valid Secrets |
Scan the code for active secrets. When a secret is valid, it means that the secret meets the necessary criteria or requirements to be considered acceptable or legitimate within a given context. For example GitHub personal access tokens of an employee that are not yet expired and can be used to access an organization’s codebase. |
Critical |
| Invalid Secrets |
Scan the code for any secrets that are no longer valid. |
Low |
| Secrets without validation rules |
Detect secrets that cannot be validated either because there is no validator or the validation failed for any reason. |
Medium |
Policy templates for secret detection
Endor Labs provides the following finding policy templates for detecting secrets.
See Finding Policies for details on how to create policies from policy templates.
| Policy Template |
Description |
Severity |
| Valid Secrets |
Use this template to scan the code for active secrets. When a secret is valid, it means that the secret meets the necessary criteria or requirements to be considered acceptable or legitimate within a given context. For example GitHub personal access tokens of an employee that are not yet expired and can be used to access an organization’s codebase. |
Critical |
| Invalid Secrets |
Use this template to scan the code for any secrets that are no longer valid. |
Low |
| Secrets without validation rules |
Use this template to detect secrets that cannot be validated either because there is no validator or the validation failed for any reason. |
Medium |
| Define custom secret token policy rules |
Use this template to detect secrets in the code using a custom secret rule to detect secret of any service that may not be included in the other rules. |
Critical |
1.7 - GitHub Action policies
Learn about the out-of-the-box finding policies for GitHub Actions.
Endor Labs provides the following out-of-the-box policies that help you assess the security posture of GitHub Actions used in your software delivery process.
See Finding Policies for details on how to enable, disable, or edit out-of-the-box policies.
Policies for RSPM
| Policy Template |
Description |
Severity |
| Default workflow token permission should be read only |
Set the default GitHub Action workflow token permission to read-only. It is highly recommended to adhere to the principle of least privilege for generating workflow tokens and enforce the workflow authors to explicitly specify the permissions they require. |
High |
| Restrict GitHub Actions to selected repositories |
Selectively enabling GitHub Actions ensures better resource management and mitigates security risks. Raise findings for organizations where GitHub Actions are enabled for all repositories. |
Medium |
| Restrict runner groups to specific repositories |
It is recommended to limit the runner groups to specific repositories. Malicious users within an organization can create repositories with workflows designed to exploit vulnerabilities. If such repositories are allowed access to the organization’s hosted runners, they could trigger automated tasks and disrupt your network. |
High |
| Restrict the use of runner groups for public repositories |
It is recommended to allow only workflows from private or internal repositories to run on GitHub hosted runners. This prevents security risks posed by malicious actors who could exploit workflows from public repositories to gain unauthorized access to your private network. |
High |
| Workflows should not be allowed to create and approve pull requests |
Do not configure the GitHub Action workflows to create and approve pull requests. Code review is a crucial part of the software development process and must be performed by human reviewers. |
High |
Policies for assessing configuration settings in workflow files
| Policy Template |
Description |
Severity |
| Non-OIDC cloud authentication detected in GitHub workflow file |
The GitHub Action workflow file authenticates to the cloud without using OIDC. Do not use hardcoded secrets to authenticate with a cloud provider. OpenID Connect(OIDC) is recommended, which provides a short-lived access token directly from the cloud provider. |
High |
| Script injection detection in GitHub workflow file |
The workflow file contains a bash injection script with an expression that could include user input. As a best practice, assign the value of untrusted input expressions to an intermediate environment variable to mitigate code and command injection vulnerabilities in GitHub workflows. |
High |
| Secrets object detected in GitHub workflow file |
This GitHub Actions job has access to all repository and organization secrets. As a best practice, avoid using ${{ toJSON(secrets) }} or ${{ secrets[...] }} and consider using GitHub Actions environment variables accessing individual secrets to restrict the secrets available to the job. |
High |
| Untrusted code checkout detected in workflow file |
This repository workflow uses ‘pull_request_target’ with an explicit PR checkout and executes build commands like ’npm install’ or ’npm build’. This is risky because the build scripts and referenced packages are controlled by the PR author. |
High |
1.8 - AI model policies
Learn about the predefined finding policy templates for CI/CD tools used in your software development environment.
Policy templates for AI models
Endor Labs provides the following finding policy templates for detecting AI models that have low Endor score.
See Finding Policies for details on how to create policies from policy templates.
| Policy Template |
Description |
Severity |
| AI models with low scores |
Raise a finding if the repository uses an AI model with an Endor score value that is less than the specified threshold value." |
Low |
2 - Exception policies
Learn about exception policies and how to use them.
Exception policies define the conditions for applying an exception to a finding. When an exception is applied to a finding, it is tracked as an exception and action policies do not apply to it. Findings with exceptions are filtered out from Endor Labs reports by default.
For example, exception policies can be used to:
- Exclude a specific finding for a specific package from build breaking policies.
- Exclude specific vulnerabilities that are accepted across your organization.
- Mark an identified issue as a false positive.
Manage exception policies
You can view, enable, clone, disable, edit, or delete your Endor Labs exception policies.
- Sign in to Endor Labs, and select Policies & Rules from the left sidebar.
- Select Exception Policies.
- Use the search bar to search for a policy or click Create Exception Policy.
- Enable or disable a policy using the toggle.
- To delete a policy, click the vertical three dots and select Delete Policy.
- To edit a policy, click on the vertical three dots and select Edit Policy.
Create an exception policy from a template
You can create an exception policy in Endor Labs to apply an exception to a finding when a given set of conditions are met.
-
Sign in to Endor Labs, and select Policies & Rules from the left sidebar.
-
Select Exception Policies.
-
Click Create Exception Policy.
-
In Define Exception Criteria, choose a policy template and define the criteria for the exception.
See exception policy templates to choose a template and define the criteria for the exception.
-
Next, you must Choose a Reason for your exception and set an expiration time for the exception.
- Select from the following reasons why you are applying this exception:
- In Triage: The finding is still being triaged for more information.
- False Positive: The finding is a false positive.
- Risk Accepted: The risk associated with the finding is accepted.
- Resolved: The issue has been resolved.
- Other: Another reason applies for this exception.
- Select when the exception should expire. Options include
30, 60, 90 days, or Never.
-
Assign Scope for which this exception policy should apply. Scopes are defined by the tags assigned to a project.
- In Inclusions, enter the tags of the projects that you want to apply an exception to.
- In Exclusions, enter the tags of the projects that you do not want to apply an exception to. Exclusions take precedence over the inclusions, in case of a conflict.
- Click the link to view the projects included in the finding policy.
- See Tagging projects for more information about creating project tags.
-
Finally, you must Name Your Exception Policy.
- Enter a human-readable Name for your exception policy.
- Enter a Description for your exception policy that explains its function.
- Enter any Policy Tags that you want to associate with your policy. Tags can have a maximum of 63 characters and can contain letters, numbers, and characters = @ _ -.
-
Advanced: When you define a policy, it applies to the current namespace and all its child namespaces. To prevent the policy from being applied to any child namespace, click Advanced and deselect Propagate this policy to all child namespaces.
-
Click Create Exception Policy. The policy is enabled by default.
Tip
When creating exceptions for a specific package, make sure to not include the version of the package in the package name template parameter. Adding the version to the name can result in the exception not applying to a newly released version of the package.
Create an exception policy from scratch
Write an exception policy from scratch using the OPA Rego policy language.
You can create an exception policy in Endor Labs to apply an exception to a finding when a given set of conditions are met.
-
Sign in to Endor Labs, and select Policies from the left sidebar.
-
Click on the Exception Policies tab.
-
Click Create Exception Policy to create a new exception policy
-
First, choose From Scratch to author an exception policy under Define Exception Criteria.
-
Next, you must Choose a Reason for your exception and set an expiration time for the exception.
- Select from the following reasons why you are applying this exception:
- In Triage: The finding is still being triaged for more information.
- False Positive: The finding is a false positive.
- Risk Accepted: The risk associated with the finding is accepted.
- Resolved: The issue has been resolved.
- Other: Another reason applies for this exception.
- Select when the exception should expire. Options include 30, 60, 90 days, or Never.
-
Enter the Rego rule for the policy in Rego Definition. For example, the following Rego rule recognizes a set of 3 vulnerabilities acknowledged by an organization, with an organization-wide exception. For more information about findings, see the Finding resource kind documentation.
package exceptions
match_vuln_id(finding, ids) {
finding.spec.finding_metadata.vulnerability.meta.name = ids[_]
}
match_vuln_id(finding, ids) {
finding.spec.finding_metadata.vulnerability.spec.aliases[_] = ids[_]
}
match_finding[result] {
some i
ids := ["CVE-2020-10683", "CVE-2019-0231", "CVE-2017-0144"]
match_vuln_id(data.resources.Finding[i], ids)
result = {
"Endor" : {
"Finding" : data.resources.Finding[i].uuid
}
}
}
-
Enter the OPA Query Statement for the rule in the following format: data.<package-name>.<function-name>. For the example above the query statement is data.exceptions.match_finding.
-
Select the Resource Kinds required to evaluate the policy. For the example above, the required resource kind is Finding. The requested resource kind records for the current scan are made available to the Rego code under data.resources.<ResourceKind>.
-
Assign Scope for which this exception policy should apply. Scopes are defined by the tags assigned to a project.
- In Inclusions, enter the tags of the projects that you want to apply an exception to.
- In Exclusions, enter the tags of the projects that you do not want to apply an exception to. Exclusions take precedence over the inclusions, in case of a conflict.
- Click the link to view the projects included in the exception policy.
- See Tagging projects for more information about creating project tags.
-
Finally, you must Name Your Exception Policy.
- Enter a human-readable Name for your exception policy.
- Enter a Description for your exception policy that explains its function.
- Enter any Policy Tags that you want to associate with your policy. Tags can have a maximum of 63 characters and can contain letters, numbers, and characters = @ _ -.
-
Advanced: When you define a policy, it applies to the current namespace and all its child namespaces. To prevent the policy from being applied to any child namespace, click Advanced and deselect Propagate this policy to all child namespaces.
-
Click Create Exception Policy. The policy is enabled by default.
All exception policies must list the matching Finding UUID under “Endor” in the following format.
foo[result] {
<match conditions>
result = {
"Endor": {
Finding: <finding-uuid>
}
}
}
Validate policy
The application verifies the Rego syntax and query statement before generating the policy. However, it is important to note that the logic cannot be completely validated without input data.
See the endorctl validate policy command for instructions on validating a custom policy and inspecting the matches returned for a specific project.
2.1 - Exception policy templates
Learn about the predefined exception policy templates and how to customize them.
Endor Labs provides the following exception policy templates that you can use to quickly create exception policies. Each exception policy template provides parameters to help you customize the conditions under which an exception is applied.
Common
Define exceptions for common use cases such as:
- Exclude a specific finding, for a specific package, for a specific dependency.
- Exclude all findings for a specific dependency.
- Exclude all findings for a specific package.
- Exclude all vulnerabilities that do not have a patch available.
The following table describes the parameters for the common exception policy template.
| Parameter |
Description |
| Vulnerability ID |
The vulnerability identifier. For example, CVE-2024-3727 or GHSA-qh2h-chj9-jffq (case insensitive). |
| Finding Name |
Match full or partial finding name. |
| Dependency Name |
Match full or partial dependency name. |
| Package Name |
Match full or partial package name. Do not specify a package version if you want the exception to apply to multiple versions of the package. |
| Fix Availability |
Select Fix Not Available to apply the exception if a patch is not available for the dependency. |
Custom
Define exceptions based on custom criteria that are less common for findings. For example, you can exclude all findings generated based on approximate scans for a specific ecosystem.
The following table describes the parameters for the custom exception policy template.
| Parameter |
Description |
| Vulnerability ID |
The vulnerability identifier. For example, CVE-2024-3727 or GHSA-qh2h-chj9-jffq (case insensitive). |
| Finding Name |
Match full or partial finding name. |
| Dependency Name |
Match full or partial dependency name. |
| Package Name |
Match full or partial package name. Do not specify a package version here if you want the exception to apply to multiple versions of the package. |
| Fix Availability |
Select Fix Not Available to apply the exception if a patch is not available for the dependency. |
| Category |
Match finding category. |
| Type |
Match finding type. |
| Severity |
Match finding severity. |
| Relationship |
Select Direct Dependency to only match findings for direct dependencies, or Transitive Dependency to only match findings for transitive dependencies. |
| Dependency Reachability |
Match findings based on the reachability of the vulnerable dependency. Select Unreachable Dependency to match findings where the vulnerable dependency is not reachable, Reachable Dependency to match findings where the vulnerable dependency is reachable, and Potentially Reachable Dependency to match findings where the vulnerable dependency is potentially reachable. You can choose any combination of these options. Be aware that the more options you select, the more exceptions you will create. This might result in the exclusion of important findings. |
| Function Reachability |
Match findings based on the reachability of the vulnerable function. Select Unreachable Function to match findings where the vulnerable function is not reachable, Reachable Function to match findings where the vulnerable function is reachable, and Potentially Reachable Function to match findings where the vulnerable function is potentially reachable. Be aware that the more options you select, the more exceptions you will create. This might result in the exclusion of important findings. |
| Ecosystem |
Match finding ecosystem. |
| Custom Tag |
Apply exceptions to findings with this meta tag, set by the policy that generated the finding or with the --finding-tags CLI option. These tags are different and separate from the system-defined finding tags. |
| File Path |
Only match findings for dependencies or files that match this glob style file pattern. For example, src/golang/**. |
| Dependency Scope |
Match findings based on the scope of the dependency. Select Normal to match findings generated for dependencies essential for the primary operation of the application, and used in a production environment. Select Test to match findings for dependencies required for testing purposes, such as testing frameworks and libraries not used in a production environment. You can choose either option or both. |
| Approximate Dependency |
Select Yes to match findings that have been generated based on approximate scans. |
SAST
Define exceptions for SAST findings.
| Parameter |
Description |
| Rule Name |
Full name of the rule. For example, Insecure cookie-based authentication (case insensitive). |
| SAST Tag |
Only match findings with this SAST tag. For example, A02:2021 or OWASP-Top-10 (case insensitive). |
| Custom Tag |
Only match findings with this meta tag, set by the policy that generated the finding or with the --finding-tags CLI option. These tags are different and separate from the system-defined finding tags. |
| File Path |
Only match findings for files that match this glob style file pattern. For example, src/golang/**. |
3 - Action policies
Learn about action policies and how to use them.
Action policies define the workflows that are triggered when the application encounters a given set of criteria (a.k.a. findings).
For example, action policies can be used to:
- Configure the behavior of scan in a CI/CD based environment.
- Set up custom ticketing workflows.
- Set up custom messaging workflows.
Manage action policies
You can view, enable, clone, disable, edit, or delete your Endor Labs action policies.
- Sign in to Endor Labs and select Policies from the left sidebar.
- Select Action Policies.
- Use the search bar to search for a policy.
- Enable or disable a policy using the toggle.
- Select Hide Disabled to hide policies that are not enabled.
- Select Hide Warnings to hide policies that are not blocking or notifications.
- To delete a policy, click the vertical three dots and select Delete Policy.
- To edit a policy, click on the vertical three dots and select Edit Policy.
Create an action policy from template
You can create an action policy in Endor Labs to perform a given action when a given set of conditions are met.
-
Sign in to Endor Labs and select Policies from the left sidebar.
-
Select Action Policies.
-
Click Create Action Policy to create a new action policy.
-
First, you must Define a Policy.
Choose a policy template and define the criteria for the action. See Action policy templates for more information.
-
Next, Choose an Action to take when the policy criteria are met.
- Choose Enforce Policy to define the behavior of endorctl scans.
- A Warn enforcement action will warn the user when the policy criteria are met by letting them know which findings violate the policy. Warn enforcement actions will only notify users of policy violations and will still return a 0 exit code in CI/CD environments, which won’t fail a job. However, it is possible to configure the scan to return a non-zero (129) exit code for policy warnings by setting the
--exit-on-policy-warning flag.
- A Break the Build enforcement action will return a non-zero (128) exit code, which will fail the job. This action will inform the user which findings violate the policy as part of the scan.
- Choose Send Notification to create a ticket or send a custom message to an integrated notification system.
- A Notification Target must be set to send a notification. A notification target may be defined as a notification integration. For more information, see Endor Labs integrations.
- Choose an Aggregation Type for notifications. Choose Project to trigger a single notification for all findings, choose Dependency to trigger multiple notifications for every dependency, or choose Dependency per package version to trigger multiple notifications for unique combinations of dependency and package. For more information, see Aggregation types for notifications.
Note
Notifications are only processed for monitored branches, not for pull requests.
-
Assign Scope for which this action policy should apply. Scopes are defined by the tags assigned to a project.
- In Inclusions, enter the tags of the projects that you want to scan.
- In Exclusions, enter the tags of the projects that you do not want to scan. Exclusions take precedence over the inclusions, in case of a conflict.
- Click the link to view the projects included in the action policy.
Note: You can set custom tags for your projects from Projects > Settings > Custom Tags. See also Tagging projects.
-
Name Your Action Policy.
- Enter a human readable Name for your action policy.
- Enter a Description for your action policy that describes what it does.
- Enter any Policy Tags that you want to associate with your policy. Tags can have a maximum of 63 characters and can contain letters, numbers, and characters = @ _ -.
-
Advanced: When you define a policy you do so for the current namespace and all child namespaces. If you do not want the policy to be applied to any child namespaces, click Advanced and deselect Propagate this policy to all child namespaces.
-
Click Create Action Policy. The policy will be enabled by default.
Create an action policy from scratch
Write an action policy from scratch using the OPA Rego policy language.
-
Sign in to Endor Labs and select Policies from the left sidebar.
-
Select Action Policies.
-
Click Create Action Policy
-
Choose From Scratch to author an action policy
-
Enter the Rego rule for the policy in Rego Definition.
For instance, the following Rego rule identifies all repository version findings that are not present in the baseline. Action policies should only operate on Findings. For more information about findings, see the Finding resource kind documentation
package examples
match_baseline(finding) {
some i
data.baseline.Finding[i].meta.description == finding.meta.description
}
match_repo_version_finding[result] {
some i
data.resources.Finding[i].meta.parent_kind == "RepositoryVersion"
not match_baseline(data.resources.Finding[i])
result = {
"Endor": {
"Finding": data.resources.Finding[i].uuid
}
}
}
-
Enter the OPA Query Statement for the rule in the following format: data.<package-name>.<function-name>.
For the example above the query statement is data.examples.match_repo_version_finding
-
Select the Resource Kinds required to evaluate the policy.
For the example above the required resource kind is Finding. The requested resource kind records for the current scan are made available to the Rego code under data.resources.<ResourceKind>. The corresponding baseline records are available under data.baseline.<ResourceKind>. Note: Action policies should only operate on Findings
-
Continue with steps 5-9 above under Create an action policy from template
All action policies must list the matching Finding UUID under “Endor” in the following format.
foo[result] {
<match conditions>
result = {
"Endor": {
Finding: <finding-uuid>
}
}
}
Validate policy
The application verifies the Rego syntax and query statement before creating the policy. However, please note that the logic cannot be fully validated without input data.
See the endorctl validate policy command for details on how to validate a custom policy and inspect the matches returned for a given project.
Baseline data
For action policies that are used to comment on, or block, PR scans you often only want to trigger the policy for findings that are not present in the baseline. The baseline data for the requested resource kinds is available under data.baseline.<ResourceKind>. Here are some examples of how to implement a function called match_baseline that returns true if a given finding also exists in the baseline. As in the example above, you can then call not match_baseline(data.resources.Finding[i]) to filter out findings that are not unique to the PR scan. Any additional resource kinds, for example DependencyMetadata, must be added to the list of requested Resource Kinds.
Note
Baseline data is only loaded for action policies with one of the Enforce Policy actions (Warn or Break the Build). It is not loaded for any other policy types.
match_baseline(finding) {
finding.meta.parent_kind == "PackageVersion"
some i
data.baseline.Finding[i].meta.description == finding.meta.description
data.baseline.Finding[i].spec.target_dependency_package_name == finding.spec.target_dependency_package_name
}
match_baseline(finding) {
finding.meta.parent_kind == "PackageVersion"
some i, j
data.baseline.DependencyMetadata[i].meta.name == finding.spec.target_dependency_package_name
data.resources.DependencyMetadata[j].meta.name == finding.spec.target_dependency_package_name
data.baseline.DependencyMetadata[i].spec.importer_data.package_name == data.resources.DependencyMetadata[j].spec.importer_data.package_name
data.baseline.DependencyMetadata[i].spec.dependency_data.reachable == data.resources.DependencyMetadata[j].spec.dependency_data.reachable
}
match_baseline(finding) {
finding.meta.parent_kind == "RepositoryVersion"
some i
data.baseline.Finding[i].meta.description == finding.meta.description
}
match_baseline(finding) {
finding.meta.parent_kind == "Repository"
some i
data.baseline.Finding[i].meta.description == finding.meta.description
}
match_baseline(finding) {
finding.spec.finding_categories[_] == "FINDING_CATEGORY_SECRETS"
some i
data.baseline.Finding[i].spec.extra_key == finding.spec.extra_key
count(data.baseline.Finding[i].spec.finding_metadata.source_policy_info.results) == count(finding.spec.finding_metadata.source_policy_info.results)
}
match_baseline(finding) {
finding.spec.finding_categories[_] == "FINDING_CATEGORY_SAST"
some i
data.baseline.Finding[i].spec.extra_key == finding.spec.extra_key
count(data.baseline.Finding[i].spec.finding_metadata.source_policy_info.results) == count(finding.spec.finding_metadata.source_policy_info.results)
}
Aggregation types for notifications
Aggregation types for notifications streamline the organization and management of findings for efficient workflow. By default, all project findings are included in a single notification. With the option to select aggregation types, notifications can be tailored to specific criteria based on dependencies. This customization simplifies developer actions and enhances productivity.
Endor Labs enables you to choose the following notification aggregation types, each offering distinct benefits.
- Project: (Default) Select Project to create a single notification for all project findings.
- Dependency: Select Dependency to create separate notifications for each dependency in a project.
- Dependency per package version: Select Dependency per package version to create separate notifications for each package in a project. Sub-tasks are created for each unique combination of dependency and package.
Example
For Jira integration notifications, a parent ticket is created with the selected issue type, either Task or Bug. The parent ticket includes the project name. Each identified dependency is grouped under a dedicated sub-ticket. The sub-ticket includes both the project name and dependency name. Findings without any dependency are grouped in a separate sub-ticket. During future scans, the existing sub-ticket status is updated or resolved. If a new dependency is found, a new sub-ticket is created.
3.1 - Action policy templates
Learn about the predefined action policy templates and how to customize them.
Endor Labs provides the following action policy templates that you can use to quickly create action policies.
Each policy template provides parameters to help you customize the conditions under which a policy action takes place.
Note: All action policy templates automatically only match new findings for PR scans. If the finding already exists in the baseline, then it is not considered to be a match. The assumption is that there is a baseline to compare against (see the --pr-baseline and/or --enable-pr-comments options).
Containers
Matches container findings for vulnerabilities that meet specific parameters. The following parameters are supported:
| Parameter |
Description |
| Vulnerability ID |
Full vulnerability identifier. For example, CVE-2024-3727 or GHSA-qh2h-chj9-jffq (case insensitive). |
| Severity |
Only match findings with this severity. |
| Fix Availability |
Select ‘Fix Available’ to only match findings if a patch is available to fix the issue in the dependency. |
| Relationship |
Select ‘Direct Dependency’ to only match findings for direct dependencies, or ‘Transitive Dependency’ to only match findings for transitive dependencies. |
| EPSS Percentile Threshold |
Only match findings with an EPSS percentile threshold equal to or higher than this threshold (0.00-100.00). The EPSS percentile threshold represents the percentile ranking among all vulnerabilities that a vulnerability will be exploited. |
| EPSS Probability Threshold |
Only match findings with an EPSS probability score equal to or higher than this threshold (0.00-1.00). The EPSS probability score represents the probability [0-1] of exploitation in the wild in the next 30 days following score publication. |
| Exploited |
Only match findings for CVEs that are listed in the Known Exploited Vulnerabilities (KEV) database. |
| Ecosystem |
Match finding ecosystem. |
| Exclude if Dependency Name Contains |
Allows you to define full or partial dependency names for which an action policy should exclude. For example, you want to exclude a specific dependency from this policy. |
| Exclude if Package Name Contains |
Allows you to define full or partial package names for which an action policy should exclude. This is the resource that the finding is raised against. For example, the package indirectly or directly includes an unmaintained dependency. |
| Exclude findings for transitive dependencies via other projects? |
Exclude findings for transitive dependencies that can only be reached via other projects. This helps your team to not act when they do not have control of findings introduced by libraries your team developed. |
| Branch Type |
Only match findings for this branch type. Set to ‘Default’ to match findings for the default branch. Set to ‘Ref’ to match findings for reference (non-default) branches. Set to ‘Pull Request’ to match findings for pull requests. Note that the ‘Send Notification’ action does not apply to pull requests, as notifications are only processed for monitored branches. |
Custom
Allows you to define a custom action policy based on the attributes of the finding. The following parameters are supported:
| Parameter |
Description |
| Finding Name |
Match full or partial finding name. |
| Category |
Match finding category. |
| Type |
Match finding type. |
| Severity |
Match finding severity. |
| Fix Availability |
Select ‘Fix Available’ to only match findings if a patch is available to fix the issue in the dependency. |
| Relationship |
Select ‘Direct Dependency’ to only match findings for direct dependencies, or ‘Transitive Dependency’ to only match findings for transitive dependencies. |
| Dependency Reachability |
Select ‘Reachable Dependency’ and ‘Potentially Reachable Dependency’ to only match findings where the vulnerable dependency is reachable. |
| Function Reachability |
Select ‘Reachable Function’ and ‘Potentially Reachable Function’ to only match findings where the vulnerable function is reachable. |
| Exclude Test |
Select ‘Yes’ to exclude test dependencies. |
| Ecosystem |
Match finding ecosystem. |
| Custom Tag |
Only match findings that have this custom tag (set by the policy that created the finding or via the --finding-tags CLI option). Note that these are different and separate from the system-defined finding tags. |
| Include Path |
Only match findings for dependencies or files that match this glob style file pattern. For example, src/golang/**. |
| Exclude Path |
Do not match findings for dependencies or files that match this glob style file pattern. For example, src/golang/**. |
| Exclude if Dependency Name Contains |
Allows you to define full or partial dependency names for which an action policy should exclude. For example, you want to exclude a specific dependency from this policy. |
| Exclude if Package Name Contains |
Allows you to define full or partial package names for which an action policy should exclude. This is the resource that the finding is raised against. For example, the package indirectly or directly includes an unmaintained dependency. |
| Exclude findings for transitive dependencies |
Exclude findings for transitive dependencies that can only be reached via other projects. This helps your team to not act when they do not have control of findings introduced by libraries your team developed. |
| Include GitHub Action findings |
Select ‘Yes’ to include findings for GitHub action dependencies. |
| Include Container findings |
Select ‘Yes’ to include findings for container dependencies. |
| Branch Type |
Only match findings for this branch type. Set to ‘Default’ to match findings for the default branch. Set to ‘Ref’ to match findings for reference (non-default) branches. Set to ‘Pull Request’ to match findings for pull requests. Note that the ‘Send Notification’ action does not apply to pull requests, as notifications are only processed for monitored branches. |
| Code Owner |
Only match findings with this code owner. For example, @octocat or @octocat-team. Case-insensitive exact matches only, no partial or approximate (fuzzy) matches. If a finding does not have a code owner, it is not matched by the policy. Code owners are automatically assigned to findings based on the CodeOwners object for the project, which is generated from the CODEOWNERS file in the default branch of the repository. For projects without a CODEOWNERS file, the CodeOwners object can be managed through the API. |
Finding types
Findings are classified into the following types when the packages scanned include:
| Finding Type |
Description |
| Custom |
Custom findings defined in custom policies. |
| Dependency With Low Activity Score |
Low Endor activity score. |
| Dependency With Low Popularity Score |
Low Endor popularity score. |
| Dependency With Low Quality Score |
Low Endor quality score. |
| Dependency With Multiple Low Scores |
More than one Low Endor Score. |
| Dependency With Very Low Activity Scores |
Very low Endor activity score. |
| Dependency With Very Low Popularity Score |
Very low Endor popularity score. |
| Dependency With Very Low Quality Score |
Very low Endor quality score. |
| License Risk |
Missing, unknown, restricted, or problematic licenses. |
| Malware Dependency |
Known malicious dependencies reported by Open Source Vulnerabilities (OSV). |
| Malware OSS Review |
Potentially suspicious code that needs review. |
| Missing Source Code |
Associated source code is not auditable. |
| Outdated Dependency |
Outdated code with older versions of the released dependencies. |
| Typosquatted Dependency |
Dependencies with intentionally similar names to popular packages. |
| Unmaintained Dependency |
Unmaintained dependencies introducing vulnerabilities. |
| Unpinned Dependency |
Variable version specifications of dependencies. |
| Unused Dependency |
Unused dependencies in the code. |
SAST
Allows you to define the action taken when a SAST finding is raised.
| Parameter |
Description |
| SAST Rule |
The type of SAST results to match. |
| Severity |
Only match findings that have this severity level. |
| Language |
Only match findings for this SAST result language. |
| SAST Tag |
Only match findings that have this SAST tag. For example, A01:2021 or Cryptographic-Failures. |
| Custom Tag |
Only match findings that have this custom tag (set by the policy that created the finding or via the --finding-tags CLI option). Note that these are different and separate from the system-defined finding tags. |
| Include Path |
Only match findings for files that match this glob style file pattern. For example, src/golang/**. |
| Exclude Path |
Do not match findings for files that match this glob style file pattern. For example, src/golang/**. |
| Branch Type |
Only match findings for this branch type. Set to ‘Default’ to match findings for the default branch. Set to ‘Ref’ to match findings for reference (non-default) branches. Set to ‘Pull Request’ to match findings for pull requests. Note that the ‘Send Notification’ action does not apply to pull requests, as notifications are only processed for monitored branches. |
| Code Owner |
Only match findings with this code owner. For example, @octocat or @octocat-team. Case-insensitive exact matches only, no partial or approximate (fuzzy) matches. If a finding does not have a code owner, it is not matched by the policy. Code owners are automatically assigned to findings based on the CodeOwners object for the project, which is generated from the CODEOWNERS file in the default branch of the repository. For projects without a CODEOWNERS file, the CodeOwners object can be managed through the API. |
Secrets
Allows you to define the action taken when a leaked secret is detected based on the validation status of the secret.
| Parameter |
Description |
| Validation Status |
Select secret validation status: Valid, Invalid, or Unable to Validate. |
| Custom Tag |
Only match findings that have this custom tag (set by the policy that created the finding or via the --finding-tags CLI option). Note that these are different and separate from the system-defined finding tags. |
| Include Path |
Only match findings for files that match this glob style file pattern. For example, src/golang/**. |
| Exclude Path |
Do not match findings for files that match this glob style file pattern. For example, src/golang/**. |
| Code Owner |
Only match findings with this code owner. For example, @octocat or @octocat-team. Case-insensitive exact matches only, no partial or approximate (fuzzy) matches. If a finding does not have a code owner, it is not matched by the policy. Code owners are automatically assigned to findings based on the CodeOwners object for the project, which is generated from the CODEOWNERS file in the default branch of the repository. For projects without a CODEOWNERS file, the CodeOwners object can be managed through the API. |
Outdated releases
Matches findings based on older versions of software or dependencies and are not actively updated. The following parameters are supported:
| Parameter |
Description |
| Relationship |
Select ‘Direct Dependency’ to only match findings for direct dependencies, or ‘Transitive Dependency’ to only match findings for transitive dependencies. |
| Dependency Reachability |
Select ‘Reachable Dependency’ and ‘Potentially Reachable Dependency’ to only match findings where the vulnerable dependency is reachable. |
| Exclude Test |
Exclude test dependencies from this policy. |
| Ecosystem |
Match finding ecosystem. |
| Exclude if Dependency Name Contains |
Allows you to define full or partial dependency names for which an action policy should exclude. For example, you want to exclude a specific dependency from this policy. |
| Exclude if Package Name Contains |
Allows you to define full or partial package names for which an action policy should exclude. This is the resource that the finding is raised against. For example, the package indirectly or directly includes an unmaintained dependency. |
| Exclude findings for transitive dependencies via other projects? |
Exclude findings for transitive dependencies that can only be reached through other projects. This helps your team to not act when they do not have control of findings introduced by libraries your team developed. |
Unmaintained dependencies
Matches findings based on dependencies that are no longer maintained or may have reached end-of-life. The following parameters are supported:
| Parameter |
Description |
| Relationship |
Select ‘Direct Dependency’ to only match findings for direct dependencies, or ‘Transitive Dependency’ to only match findings for transitive dependencies. |
| Dependency Reachability |
Select ‘Reachable Dependency’ and ‘Potentially Reachable Dependency’ to only match findings where the vulnerable dependency is reachable. |
| Exclude Test |
Exclude test dependencies from this policy. |
| Ecosystem |
Match finding ecosystem. |
| Exclude if Dependency Name Contains |
Allows you to define full or partial dependency names for which an action policy should exclude. For example, you want to exclude a specific dependency from this policy. |
| Exclude if Package Name Contains |
Allows you to define full or partial package names for which an action policy should exclude. This is the resource that the finding is raised against. For example, the package indirectly or directly includes an unmaintained dependency. |
| Exclude findings for transitive dependencies via other projects? |
Exclude findings for transitive dependencies that can only be reached via other projects. This helps your team to not act when they do not have control of findings introduced by libraries your team developed. |
Unpinned direct dependencies
Matches findings based on direct dependencies that do not have a version or a range of versions specified. Supported configuration parameters for this action policy template are:
| Parameter |
Description |
| Exclude Test |
Exclude test dependencies from this policy. |
| Ecosystem |
Match finding ecosystem. |
| Exclude if Dependency Name Contains |
Allows you to define full or partial dependency names for which an action policy should exclude. For example, you want to exclude a specific dependency from this policy. |
| Exclude if Package Name Contains |
Allows you to define full or partial package names for which an action policy should exclude. This is the resource that the finding is raised against. For example, the package indirectly or directly includes an unmaintained dependency. |
| Exclude findings for transitive dependencies via other projects? |
Exclude findings for transitive dependencies that can only be reached through other projects. This helps your team to not act when they do not have control of findings introduced by libraries your team developed. |
Unreachable direct dependencies
Matches findings based on dependencies that are not directly used or called within a project. Supported configuration parameters for this action policy template are:
| Parameter |
Description |
| Exclude Test |
Exclude test dependencies from this policy. |
| Ecosystem |
Match finding ecosystem. |
| Exclude if Dependency Name Contains |
Allows you to define full or partial dependency names for which an action policy should exclude. For example, you want to exclude a specific dependency from this policy. |
| Exclude if Package Name Contains |
Allows you to define full or partial package names for which an action policy should exclude. This is the resource that the finding is raised against. For example, the package indirectly or directly includes an unmaintained dependency. |
| Exclude findings for transitive dependencies via other projects? |
Exclude findings for transitive dependencies that can only be reached through other projects. This helps your team to not act when they do not have control of findings introduced by libraries your team developed. |
Vulnerabilities
Matches findings that are vulnerabilities that meet specific parameters. The following parameters are supported:
| Parameter |
Description |
| Vulnerability ID |
Full vulnerability identifier. For example, CVE-2024-3727 or GHSA-qh2h-chj9-jffq (case insensitive). |
| Severity |
Only match findings with this severity. |
| Fix Availability |
Select ‘Fix Available’ to only match findings if a patch is available to fix the issue in the dependency. |
| Relationship |
Select ‘Direct Dependency’ to only match findings for direct dependencies, or ‘Transitive Dependency’ to only match findings for transitive dependencies. |
| Dependency Reachability |
Select ‘Reachable Dependency’ and ‘Potentially Reachable Dependency’ to only match findings where the vulnerable dependency is reachable. |
| Function Reachability |
Select ‘Reachable Function’ and ‘Potentially Reachable Function’ to only match findings where the vulnerable function is reachable. |
| Exclude Test |
Select ‘Yes’ to exclude test dependencies from this policy. |
| EPSS Percentile Threshold |
Only match findings with an EPSS percentile threshold equal to or higher than this threshold (0.00-100.00). The EPSS percentile threshold represents the percentile ranking among all vulnerabilities that a vulnerability will be exploited. |
| EPSS Probability Threshold |
Only match findings with an EPSS probability score equal to or higher than this threshold (0.00-1.00). The EPSS probability score represents the probability [0-1] of exploitation in the wild in the next 30 days following score publication. |
| Exploited |
Only match findings for CVEs that are listed in the Known Exploited Vulnerabilities (KEV) database. |
| Ecosystem |
Match finding ecosystem. |
| Exclude if Dependency Name Contains |
Allows you to define full or partial dependency names for which an action policy should exclude. For example, you want to exclude a specific dependency from this policy. |
| Exclude if Package Name Contains |
Allows you to define full or partial package names for which an action policy should exclude. This is the resource that the finding is raised against. For example, the package indirectly or directly includes an unmaintained dependency. |
| Exclude findings for transitive dependencies via other projects? |
Exclude findings for transitive dependencies that can only be reached via other projects. This helps your team to not act when they do not have control of findings introduced by libraries your team developed. |
| Include GitHub Action findings |
Select ‘Yes’ to include findings for GitHub action dependencies. |
| Include Container findings |
Select ‘Yes’ to include findings for container dependencies. |
| Branch Type |
Only match findings for this branch type. Set to ‘Default’ to match findings for the default branch. Set to ‘Ref’ to match findings for reference (non-default) branches. Set to ‘Pull Request’ to match findings for pull requests. Note that the ‘Send Notification’ action does not apply to pull requests, as notifications are only processed for monitored branches. |
| Code Owner |
Only match findings with this code owner. For example, @octocat or @octocat-team. Case-insensitive exact matches only, no partial or approximate (fuzzy) matches. If a finding does not have a code owner, it is not matched by the policy. Code owners are automatically assigned to findings based on the CodeOwners object for the project, which is generated from the CODEOWNERS file in the default branch of the repository. For projects without a CODEOWNERS file, the CodeOwners object can be managed through the API. |
4 - Remediation policies
Learn about remediation policies and how to use them.
Remediation policies define the conditions for applying remediation to a finding when an upgrade is available that fixes the finding.
You can view, enable, clone, disable, edit, or delete your Endor Labs remediation policies.
- Sign in to Endor Labs and select Policies & Rules from the left sidebar.
- Click Remediation Policies.
- Use the search bar to search for a policy or click Create Remediation Policy.
- Enable or disable a policy using the toggle.
- To delete a policy, click the vertical three dots and select Delete Policy.
- To edit a policy, click on the vertical three dots and select Edit Policy.
- To clone a policy, click on the vertical three dots and select Clone Policy.
You can create a remediation policy in Endor Labs to address a finding when specific conditions are met.
-
Sign in to Endor Labs, and select Policies & Rules from the left sidebar.
-
Click on the Remediation Policies tab.
-
Click Create Remediation Policy to create a new remediation policy.
-
Select a policy template.
Currently, you can choose Recommended Version Upgrades for Vulnerabilities.
-
Next, choose the template parameters.
- Upgrade Risk: The acceptable level of risk that a breaking change might occur with the upgrade.
- Severity: Match upgrades that would fix findings with a particular severity.
- Exclude Test: Select Yes to exclude version upgrade recommendations for fixing findings in test dependencies.
- Dependency Reachability:: Match upgrades that address findings with the following level of dependency reachability.
- Reachable dependency
- Unreachable dependency
- Potentially reachable dependency
- Function Reachability: Match upgrades that address findings with the following level of function reachability.
- Reachable function
- Unreachable function
- Potentially reachable function
- Minimum Number of Findings: Only match upgrades that resolve a minimum number of findings equal to or greater than this value.
-
Select a notification target to be associated with the remediation policy.
See Integrations for more information on creation notification integrations.
-
Assign Scope for which this remediation policy should apply. Scopes are defined by the tags assigned to a project.
- In Inclusions, enter the tags of the projects that you want to apply the remediation policy.
- In Exclusions, enter the tags of the projects that you do not want to apply the remediation policy. Exclusions take precedence over the inclusions, in case of a conflict.
- Click the link to view the projects included in the remediation policy.
- See Tagging projects for more information about creating project tags.
-
Finally, you must Name Your Remediation Policy.
- Enter a human-readable Name for your remediation policy.
- Enter a Description for your remediation policy that explains its function.
- Enter any Policy Tags that you want to associate with your policy. Tags can have a maximum of 63 characters and can contain letters, numbers, and characters = @ _ -.
-
Advanced: When you define a policy, it applies to the current namespace and all its child namespaces.
To prevent the policy from being applied to any child namespace, click Advanced and deselect Propagate this policy to all child namespaces.
-
Click Create Remediation Policy.
The policy is enabled by default.
5 - Tag projects
Learn about tagging projects to manage policies in Endor Labs
All Endor Labs policies provide the option to define inclusion and exclusion criteria based on project tags. This allows you to implement exception workflows, to onboard new teams or business units, and to set specific policies that only apply to sets of projects, such as those that are mature or the crown jewel applications of an organization.
Most organizations have projects with differing compliance and security requirements. Adopting a single standard for all projects can lead to challenges. While many controls apply equally across an environment, some controls are excessive or irrelevant for projects that don’t need to meet specific regulatory frameworks, or do not process sensitive information.
For example, an organization may want to look for leaked secrets in all repositories, but may not require a robust vulnerability management program and branch protection strategy on projects where internal documentation is developed.
The following reference tagging strategies can help organizations align their policies with their internal control needs.
| Use Case |
Rationale |
Example Tags |
| Data Classification |
Apply controls to projects from which applications that proccess sensitive are developed. |
Classification_Restricted, Classification_HighlySensitive, Classification_Public |
| Application Importance |
Apply controls to projects based on the importance of the applications developed in them. |
Application_CrownJewel, Application_Critical |
| Application Exposure |
Apply controls to project from which applications that are exposed internally or to the public internet differently. |
Exposure_Public , Exposure_Internal |
| Compliance |
Apply controls to projects where specific compliance or regulatory controls may apply. |
Compliance_SOC2, Compliance_HIPAA, Compliance_PCI, Compliance_None |
| Business Unit |
Apply controls to projects based on a business units maturity or onboarding status. Apply different controls to a new aquisition. |
BU_Infrastructure, BU_Clinical |
| Policy Exceptions |
Do not apply a control to a repository that has an approved policy exception |
Policy_Exception_Branch_Protection |
Tag your projects
Tags add additional metadata to projects and help you identify them. You can also use the project tags to define the scope of a finding or an action policy for a project.
To create tags for a project:
- Sign in to Endor Labs and select Projects from the sidebar.
- Select a project and click Settings.
- Type a name for the tag in Custom Tags and press Enter. Tags can have a maximum length of 63 characters and can contain letters (A-Z), numbers (0-9), and characters (=@-_).
- Click Save Tags.
- Use Reset Tags to make a new entry.
